Ask an Expert
Planning the right solution requires an understanding of your project's security goals. Let Kingston's experts guide you.


Prof. Sally Eaves is Chair of Cyber Trust and Senior Policy Advisor for the Global Foundation of Cyber Studies and Research. Described as the “torchbearer for ethical tech,” she is the inaugural recipient of the Frontier Technology and Social Impact Award, presented at the United Nations. A chief technology officer by background, and now Professor in Advanced Technologies and a global strategic advisor across emergent technologies, Sally is an award-winning international author, MC, keynote speaker, and thought leader on digital transformation (AI, 5G, cloud, blockchain, cybersecurity, governance, IoT, data science) alongside culture, skills, DEI, sustainability, and social impact.
Sally educates and mentors actively to support the next generation of tech talent and has founded Aspirational Futures to enhance inclusion, diversity, and equality in education and technology, with her latest book on “Tech For Good” set to be released soon. Sally is consistently recognized for global influence in the technology space by leading bodies such as Onalytica, appearing in the top 10 worldwide across multiple disciplines from AI to 5G to sustainability and beyond.
Multiple vectors of cybersecurity risk are converging in scope, scale, and sophistication, creating an ever-present danger to organizations in any sector and of any size, from SME through to enterprise. In this piece, we explore what has changed, with particular attention to the growing risk exposure of SMEs, and share tangible examples of how to enhance your security posture, whatever your starting point, from attention to culture and education, to zero trust practices and embedding endpoint cybersecurity.
Firstly, it’s wise to look at the catalysts behind the acceleration in security risks, most notably the pandemic and its impacts around “work from anywhere” models alongside growing employee and consumer agency with evolved expectations and behaviors, alongside the situation in Ukraine and rapidly developing energy crisis – unfortunately, it remains a truism that attackers always feed off our areas of most vulnerability. Exploring the threat landscape in more detail, five pillars of risk come to the fore as explored below.
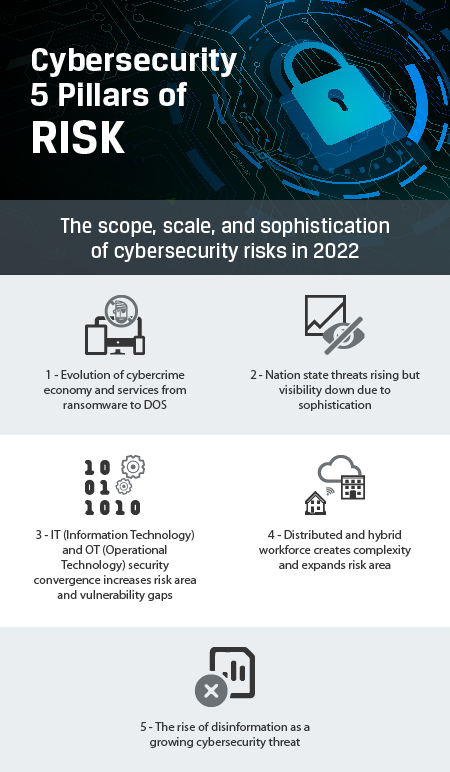
SMEs have been especially impacted by the growth in cybersecurity attacks, notably ransomware and phishing, with new research showing that some 43% of cyber-attacks{{Footnote.N68026}} target small businesses (Verizon 2022). Taking the UK as a broadly representative example, the 2021 NCSC Annual Review{{Footnote.N68027}} recently declared ransomware to be the most significant cyber threat facing the UK today. With this sector representing over 99% of businesses{{Footnote.N68028}} in the UK and the USA (SBA 2021), the collective contribution to global economic growth moves center stage, alongside the risk posed to supply chains with SME’s providing an increasingly attractive entry point to wider enterprise ecosystems.
Drilling into the risk in more detail, research by Datto{{Footnote.N68029}} found that 85% of MSPs report ransomware as the biggest malware threat to small businesses. With Remote Desktop Protocol (RDP) the single most common vector for this type of attack, the increased distribution of SME employees with remote-to-hybrid working models alongside the rise of “Bring Your Own Device” when physically in the office has created new challenges. These range from the expanded threat area to the risk of complacency and breaking of habits around security practices, with the continual change in working logistics. This is coupled with the baseline that SME’s typically have misconceptions around the levels of support “in range” to them, alongside greater budget constraints, fewer resources, and a lack of in-house specialist technical skills – all raising their desirability as a focus of attack for bad actors. And given the impact of the sector already outlined to both local and global economies, this makes their disproportionate operational, financial, and reputational effect one of significant concern.
But it is not all negative news! Firstly, SMEs can – by their very nature and infrastructure – be more agile to change and the introduction of new approaches, and are typically less likely to be carrying the weight of legacy technologies or process-heavy long decision-making cycles. Additionally, there is much that SMEs can do today to improve their cybersecurity posture for tomorrow. The time is now to move beyond common perceptions that effective security is simply too difficult, too time consuming, or too expensive to embed, or conversely that you can buy something like “Zero Trust” straight off the shelf once and you are done – it simply does not work that way, it is an ongoing journey, not a destination.
So, what can SMEs do to both change the narrative around security and improve their posture around the risks? Firstly, considering some of the education and awareness opportunities available, the UK's National Cyber Security Centre{{Footnote.N68030}} provides an excellent starting point for free up-to-date resources. This is key given research{{Footnote.N68031}} that finds that smaller businesses are not consulting authoritative sources, and instead when using a general search, they are frequently overwhelmed by the volume of advice information online, with no way to judge or prioritize it. So, education around your employees and availability of supporting documentation is an absolute must. The power of partnership is also key, even large enterprises typically utilize third-party providers that specialize in cybersecurity tools, trainings, and best practices and there is a lot of support available here that can be tailored to organizations of any size. And what better way to negate the rise in bad actor collaboration than for organizations to come together for good and openly share best practices!
Security threat actors are continually evolving their attack approaches to make them more impactful, including the coming together of cyber-criminal gangs with increasingly complex and professional tactics. We must respond in kind as a sector and as organizations and individuals – this requires a focus on technology, culture, processes, and skills.
As I previously discussed in the Kingston Cognate Twitter Chat (@kingstontechbiz), around 98% of cyber-attacks can actually be negated through good cyber hygiene. Here are some suggestions on getting this foundation right from a technology and process perspective:
In particular, hardware-encrypted devices such as USBs and external SSDs afford a highly cost-effective solution to move forward with data-loss protection expediently – and are relevant for multi sector application and for organizations of any size. Rob Allen, Director of Marketing & Technical Services, Kingston Technology Europe, explains:
We offer encrypted USB solutions for government, defense, and intelligence agencies right through to FinTech and health care, and to your small/medium businesses and SOHO (Small Office Home Office) users… The one I'm really impressed with and excited about is an external SSD with touchscreen pin and password, an exciting addition to what we usually do.
Additionally, Kingston Technology’s excellent Ask an Expert team can provide personalized advice on the potential benefits tailored to your organization's specific storage environment and needs – with contact requests going straight to the technical resource group – alongside providing multiple, freely accessible resource guides, applicable to data center customers, corporate end users, and SMEs alike. And there is more support available for you in their Data Security Blog, where you can find top 12 tips for SMEs to enhance cybersecurity.
Everyone has the ability to make a difference when it comes to reducing threats and every individual is a security gatekeeper of sorts – this is a shared responsibility which must be reflected in a culture that enables “speaking up”. Further to Rob explaining about the benefits of Kingston IronKey Encrypted portfolio, he raises a hugely important point:
So, what you want to prevent is that people find workarounds that are less secure. And equally, and this is a very important one, what you want to do is create an atmosphere where they can come forward… and with best practices make it relevant things that people can apply in their home life too – give real world examples.
This equally extends to skills accessibility and skills confidence around cybersecurity and data literacy more broadly, ensuring that access to the latest learnings is made available to all employees regardless of whether they hold a technological position or not. This can be further supported by developing more personalized education programs that help people to identify their own learning style preferences so that they can grow and develop in the way that suits them best – smart thinking to complement smart technology – and which improves outcomes across individuals, teams, and organizations alike. Now that is shared value impact!
Kingston Technology is a long established and highly trusted leader in the encrypted USB drive space and can offer bespoke support on the benefits and alignment to your business needs. This, combined with their superb Ask an Expert team, means you can get truly tailored advice, specific to your environment and needs.
#KingstonIsWithYou #KingstonIronKey

Planning the right solution requires an understanding of your project's security goals. Let Kingston's experts guide you.